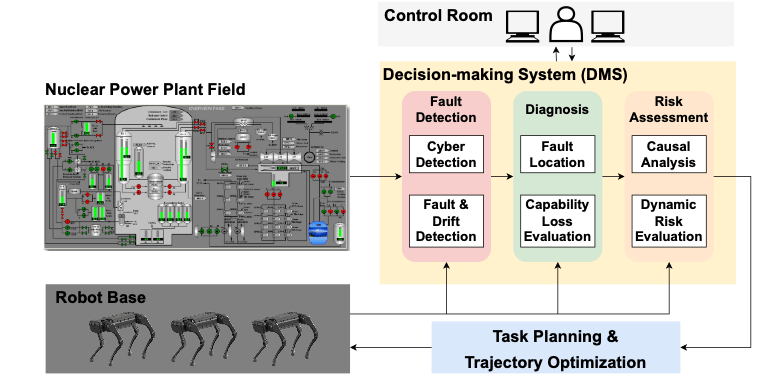
Robot-assisted Online Monitoring & Maintenance
Operation and Maintenance (O&M) costs make up almost 66 % of the total operation cost of Nuclear Power Plants. Total O&M costs are expected to continue to increase as plants age. With the rapid development in Robotics and Autonomous systems, we strive to put a dent to these expenses by deploying mobile robots which can carry out basic walk-down and maintenance tasks with limited to no supervision. We are currently transferring a 2D simulation to a 3D simulation for robotic trajectory optimization and path planning.
Resilience Strategy Against Cyber-Attacks
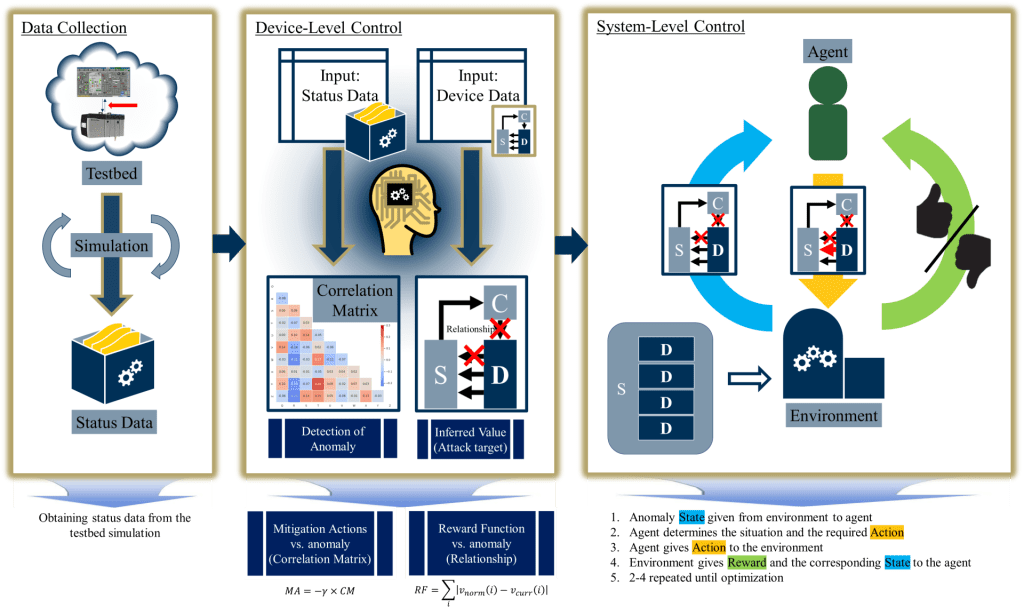
Critical infrastructure composed of cyber physical systems are vulnerable to attacks that endanger their safety. Breaches in power systems can lead to power outages, environmental disasters, and loss of life. As critical infrastructures are transitioning to digital instrumentation and control (I&C) systems for better control methods, the need for defense strategies against cyber threats are also introduced. We are working on developing a resilience strategy based on machine learning and reinforcement learning for I&C systems with the example of applying the strategy to nuclear facilities. The resilience strategy is composed of device-level control, where the attack target itself is controlled to gain resilience, and system-level control, where the control of adjacent systems is performed.
Nuclear Power Plant SBOM Development
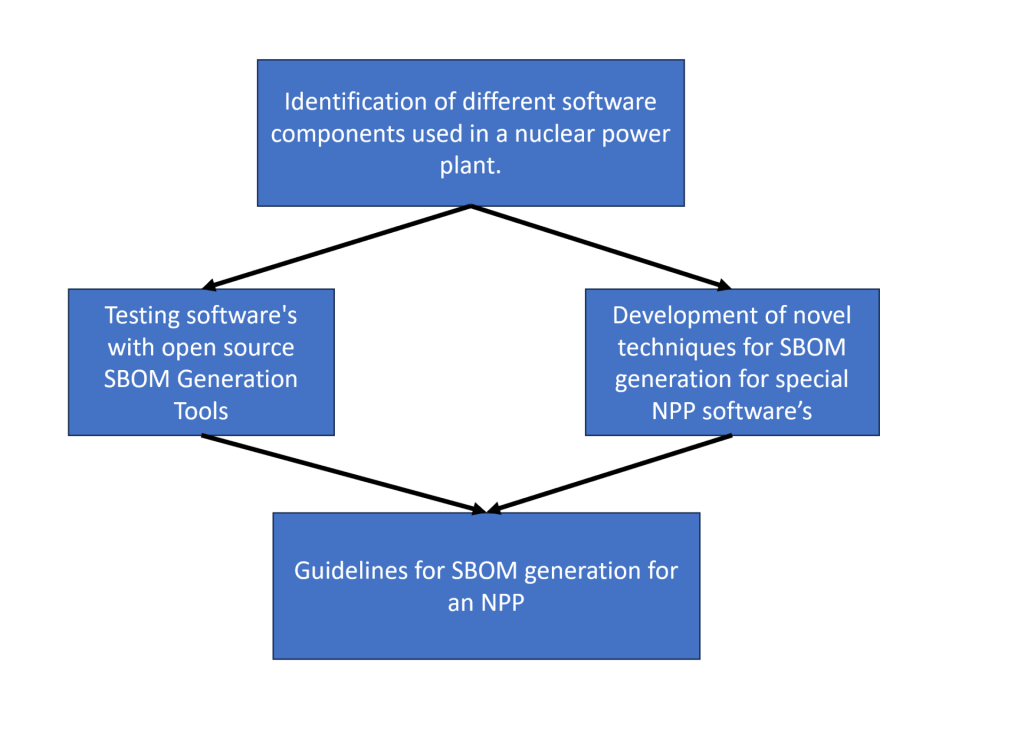
A “Software Bill of Materials” (SBOM) is a nested inventory for software, a list of ingredients that make up software components. To enhance vulnerability management and facilitate quick identification of impacted components when new software vulnerabilities are identified, SBOMs can be integrated with vulnerability data sources and vendor vulnerability attestations. In the context of Nuclear Power Plant (NPP), due to the presence of legacy and firmware systems, the traditional workflow of generating SBOM is not accurate. So, the goal of this project is propose methodology and guidelines for an NPP to generate accurate and efficient SBOM’s. In addition, this project also compares qualitatively and quantitatively the current open-source tools used for SBOM generation for an NPP with a practical use case example. This technique will help an NPP in implementing SBOM efficiently and enhance the overall security of the plant.
Cybersecurity for Advanced Reactors
Current efforts to evaluate cyber risks within nuclear power plants are limited due to the traditionally analog systems implemented in the current fleet. To evaluate cyber risks associated with Generation IV and advanced reactor designs, iFAN lab has developed a cybersecurity testbed including hardware-in-the-loop (HiL) integration, digital twins, and autonomous control. The autonomous control system uses machine learning-based digital twins to detect, predict, and select a strategy to autonomously control reactor subsystems. The autonomous control system allows for expanded attack vectors to machine learning models, communication pathways, and hardware systems.

Attacks against Machine Learning
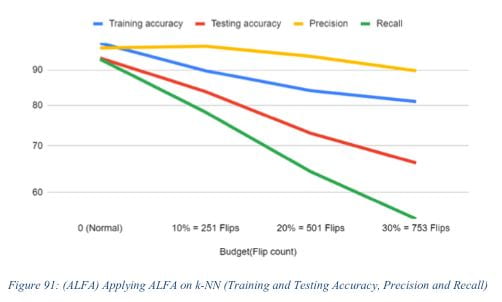
As machine learning based digital twinning efforts become more popular within the nuclear industry, it becomes increasingly necessary to identify potential threats against autonomous control systems and machine learning models. iFAN lab has developed a new attack scenario against autonomous control systems in the nuclear industry by attacking training and testing data being fed into the machine learning models. Adversarial label flip attacks (ALFA) flip a certain percentage of training data to train the machine learning model on false data. Gradient descent attacks flip testing data to trick the data scientist into questioning the validity of the model. Both methods prove a need to protect the training and testing data for autonomous control systems and machine learning-based digital twins within the nuclear industry.
Adversarial Machine Learning
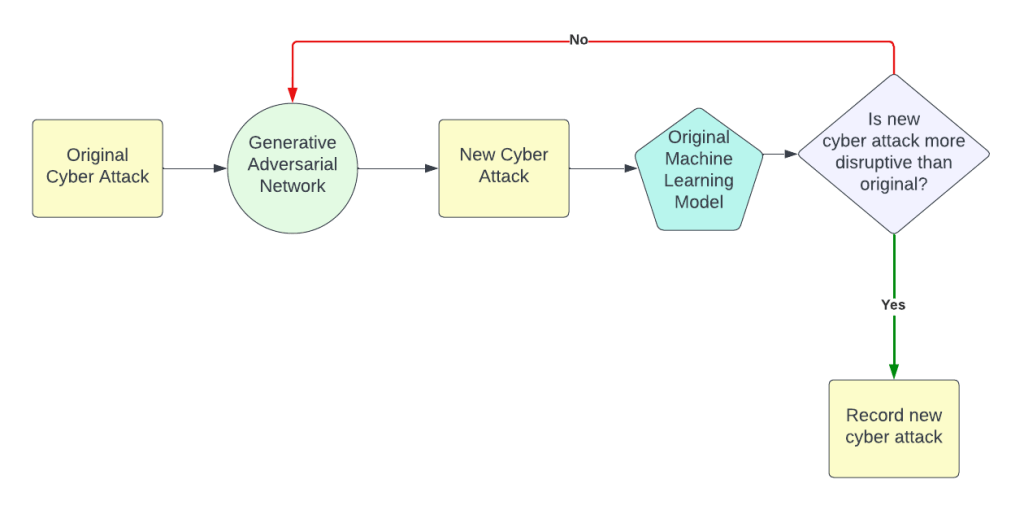
Anticipating new attack vectors is important in understanding potential adversarial actions. To understand more unique and innovative threats, a generative adversarial (GAN) is fed adversarial data to come up with a new plausible attack vector to be tested against the original adversarial model. The ultimate goal is to create a robust digital twin that can overcome new attack vectors by training on GAN-generated data.
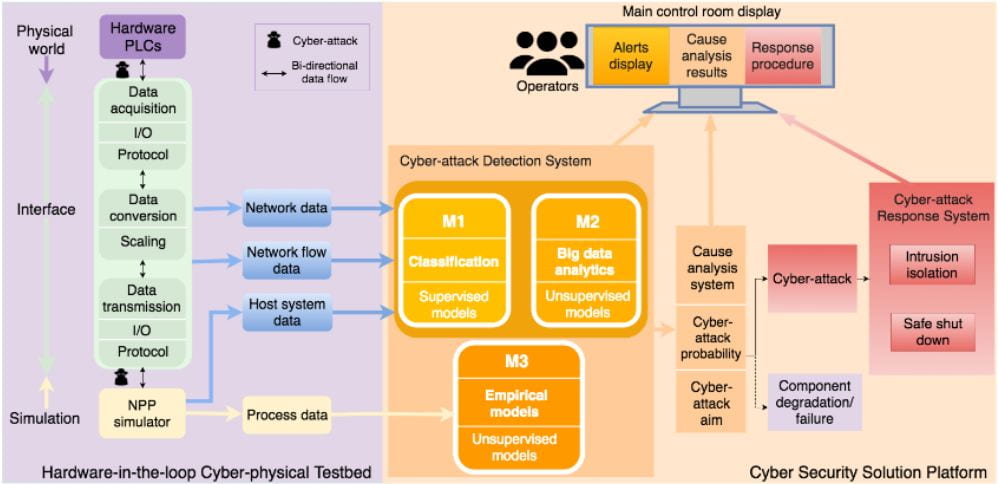
Cyber-attack Detection with Both Network Data and Process Data
Detecting abnormal conditions within a nuclear power plant is an important aspect of the supervisory control and data acquisition (SCADA) systems. Due to the integration of digital electronics in SCADA systems, these systems can also be vulnerable to cyber attacks. To alert the operators of a potential cyber attack, a cyber attack detection system (CADS) was developed to determine if the abnormal conditions were caused by a cyber attack and determine a response. By using a combination of supervised and unsupervised machine learning models on network and process data, the CADS system alerts the operator of an abnormal condition, determines the cause of the abnormal condition, and responds to the condition if it is a cyber threat. The CADS uses a hardware-in-the-loop system connected to a nuclear power plant simulator to simulate traditional SCADA systems.